By now it is clear that organizations are fully committed to embracing multi-cloud architecture as part of their digital transformation strategies and initiatives. A closely related security trend has emerged against this backdrop: cloud data breaches and security incidents such as those that impacted Okta, Twilio, and others.
As organizations adopt multiple cloud services, they need to be cognizant of security hygiene, which is the implementation of best practices and secure configurations in cloud environments. Security hygiene mitigates risks associated with use of the cloud and, more broadly, any technology.
The Shared Responsibility Model
The cloud uses something referred to as a “shared responsibility model,” which delineates what the cloud provider is responsible for, what the cloud consumer is responsible for, and what responsibilities are shared between these two entities.
These responsibilities differ depending on the service model in question, no matter if it’s infrastructure-as-a-service (IaaS), platform-as-a-service (PaaS), or software-as-a-service (SaaS). For example, let’s look at the Microsoft Azure Shared Responsibility Model, which clearly delineates customer, vendor, and shared responsibilities.
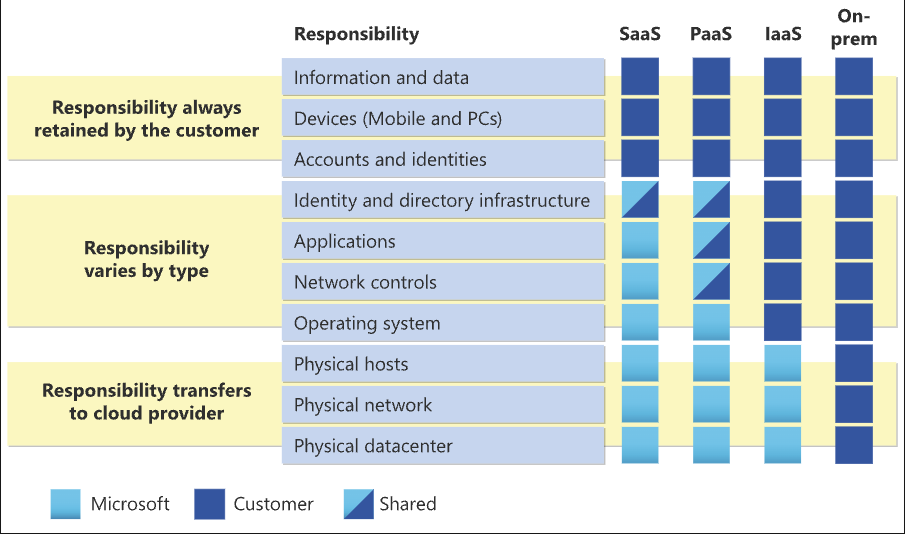
While organizations continue to move to multi-cloud future to leverage the strengths of multiple cloud services and providers, they need to be familiar with their responsibilities under the shared responsibility model and ensure that they are doing their part. Unfortunately today, this isn’t the case: sources such as Gartner predict that through 2025, 99% of cloud security incidents will be due to customer misconfiguration.
Which companies are the most important vendors in cybersecurity? Click here to see the Acceleration Economy Top 10 Cybersecurity Shortlist, as selected by our expert team of practitioner analysts.
The Importance of Multi-Cloud Security Hygiene
To avoid misconfiguration, organizations must have robust cloud security hygiene, which is complex when dealing with multiple providers. A good part of multi-cloud adoption includes implementing secure configurations and being familiar with each of the respective cloud platforms and services, their configurations, and, of course, industry best practices for cloud security.
Luckily, there are also tools to help organizations handle these challenges since having humans understand all of these nuanced configurations — and even more importantly, monitor them at scale, especially in large complex environments — simply isn’t realistic.
These tools include Cloud Security Posture Management (CSPM) and SaaS Security Posture Management (SSPM). CSPM and SSPM can help you identify vulnerable configurations; determine if your environments align with industry guidance such as Center for Internet Security benchmarks; and ensure your cloud configurations align with specific compliance requirements that your organization and industry may follow.
CSPM Tools
CSPM tools help users identify and remediate risks, automate visibility and monitoring, and produce alerts and notifications for insecure configurations or potentially concerning behavior.
CSPM typically applies to IaaS environments such as AWS, Azure, and Google Cloud. Popular CSPM tools include vendors such as Wiz, Sysdig, and Palo Alto Networks (on the Acceleration Economy Top 10 Cybersecurity Short List), among others. There are also open source software (OSS) options such as Prowler.
CSPM tools have continued to evolve as cloud adoption has grown. In the early days of CSPM tooling, there wasn’t broad support for different CSPs and they weren’t as feature-rich. They’ve grown to cover more cloud service offerings and provide detailed analyses of your configurations and compliance in specific cloud environments.
SSPM Tools
SSPM tooling goes beyond IaaS cloud offerings and focuses on SaaS applications. This is crucial because while organizations in general may be using two to three IaaS providers on average, large enterprise environments are often using hundreds of SaaS applications.
On the SSPM front, there are organizations such as AppOmni, Obsidian Security, Grip Security (also on our shortlist), and Axonius that provide robust and promising SSPM capabilities. These capabilities continue to evolve along with the threat landscape to help organizations get a handle on their SaaS security and compliance requirements.
Early on, SSPM players didn’t boast broad SaaS coverage, but that is changing with vendors such as Axonius, which uses its asset management connectors and other unique features to cover a wide range of SaaS offerings. This allows organizations to ensure they meet compliance requirements and have secure configurations across their portfolios of SaaS applications. SSPM tools are suited for any organization that is using SaaS at scale; that is, nearly every modern organization.
Final Thoughts
Knowing that nearly all cloud security incidents will be due to customer misconfigurations and errors, it’s vital for organizations in multi-cloud environments to leverage CSPM and SSPM tools to ensure proper hygiene, while also being aware of what they are on the hook for under the relevant shared responsibility models. Failing to do so can have devastating consequences, as we have seen over the last several years with millions of sensitive records, proprietary data, and more being exposed.
Want more cybersecurity insights? Visit the Cybersecurity channel: