In episode 41 of the Cybersecurity Minute, Robert Wood discusses secrets that are checked into codebases and why they require proper security.
Which companies are the most important vendors in cybersecurity? Click here to see the Acceleration Economy Top 10 Cybersecurity Shortlist, as selected by our expert team of practitioner analysts.
Highlights
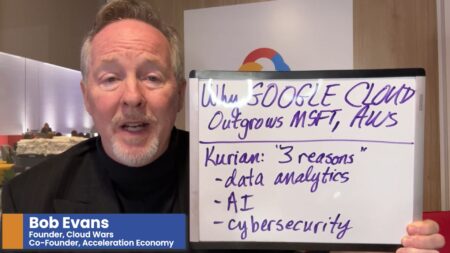
00:17 — Secrets can mean different things to different people. It could refer to passwords, database credentials, connection strings, or API tokens. Whatever form they take, they are meant to be kept a secret.
00:34 — Developers or coders who contribute to the development of the codebase — and its secrets — will be able to see it by design. Additionally, they will be able to see the history of the codebase.

Which companies are the most important vendors in cybersecurity? Check out
the Acceleration Economy Cybersecurity
Top 10 Shortlist.
00:59 — Robert emphasizes the importance of going back into the codebase after something has been “accidentally committed.” Ensure that you are changing values, updating keys, and changing any potential points of exposure.
01:06 — It is really important that those setting up CI/CD pipelines, and the security around them, have proper security stages integrated into them. Consider a solution that will address any potential leaks into a codebase.
Want more cybersecurity insights? Visit the Cybersecurity channel: