JupiterOne is part of a new cybersecurity vendor profile series from Acceleration Economy’s Cybersecurity as a Business Enabler channel.
Who They Are
Cybersecurity management today can feel like playing 3D chess where playing boards are constantly being added. As attack surfaces continue to expand with increasing usage of the cloud – multi-cloud and hybrid clouds included – and the accelerated pace of cyber threats explodes, this means companies of all sizes need to be constantly vigilant.
To that end, JupiterOne, founded in 2018 by CEO Erkang Zheng, set out to help organizations navigate the complex landscape of cybersecurity. Its mission is threefold:
- Simplify the security process to answer the question: Are we compliant and secure?
- Combat complexity which is the enemy of agility.
- Put the power of power of unparalleled visibility at the center.

“We had this significant explosion of cloud and digital transformation, and the whole COVID situation actually accelerated that growth. For the entire cybersecurity market, it has accelerated the demand for better security measures.
We also believe security is a basic right; it’s not optional. Whether you’re a 10-person startup or a Fortune500 company, you need the right security product and visibility to do business securely.”
Erkang Zheng – CEO of JupiterOne | Speaking with WRAL TechWire
What They Do
JupiterOne’s core platform puts “cyber assets at the center of digital security” through its open, extensible, robust, and secure architecture. This platform comprises three critical solutions to unleash security to accelerate innovation – creating a single source of truth.
It seems that new regulations and compliance rules and policies are being added all the time, but for good reason. However, this can create headaches for security teams and programs when companies have a global presence.
Cyber Asset Governance & Compliance Management
The Cyber Asset Governance & Compliance solution is a “compliance-as-code” tool that automatically “gathers evidence to support compliance needs and processes” with 3 key factors in mind.

More cyber assets can increase attacks

Manual security audits are costly

Compliance is a single point-in-time view
Security Operations, Engineering, & Vulnerability Management
The Security Operations & Engineering solution provides easy-to-use APIs to create a “world-class security operations and engineering program” based on 3 important components.

Vast security and compliance frameworks

Cyber asset context unlocks SecOps
Additionally, JupiterOne realizes the need for in-depth, practical guidance to “helps practitioners, vendors, and investors understand the range of capabilities needed to build, manage, and operate a security program.” As such, JupiterOne has released the “Cyber Defense Matrix” eBook that is “simple in form, easy to grasp, and highly versatile.”

Additionally, JupiterOne realizes the need for in-depth, practical guidance to “helps practitioners, vendors, and investors understand the range of capabilities needed to build, manage, and operate a security program.” As such, JupiterOne has released the “Cyber Defense Matrix” eBook that is “simple in form, easy to grasp, and highly versatile.”
Who They Have Impacted
As the “Data + AI” company, the Databricks goal is to unify “your data, analytics and AI workloads”. However, they realized that needed the right tools to build a platform for them and its customers to succeed. This meant they needed “a solution that enables greater visibility and discoverability across the company’s cloud assets, as well as the owners of those assets.”
“Centralization and visibility can enable greater security and speedier remediation.”
Adam Youngberg, Senior Manager, Security Engineering at Databricks
The challenges that Databricks faced were critical for long-term success and necessary for speed and agility.
They needed a cloud-first cyber asset management solution
With the JupiterOne Cloud Asset Management and Galaxy View solutions, all cyber asset relationships can be managed from a single location.
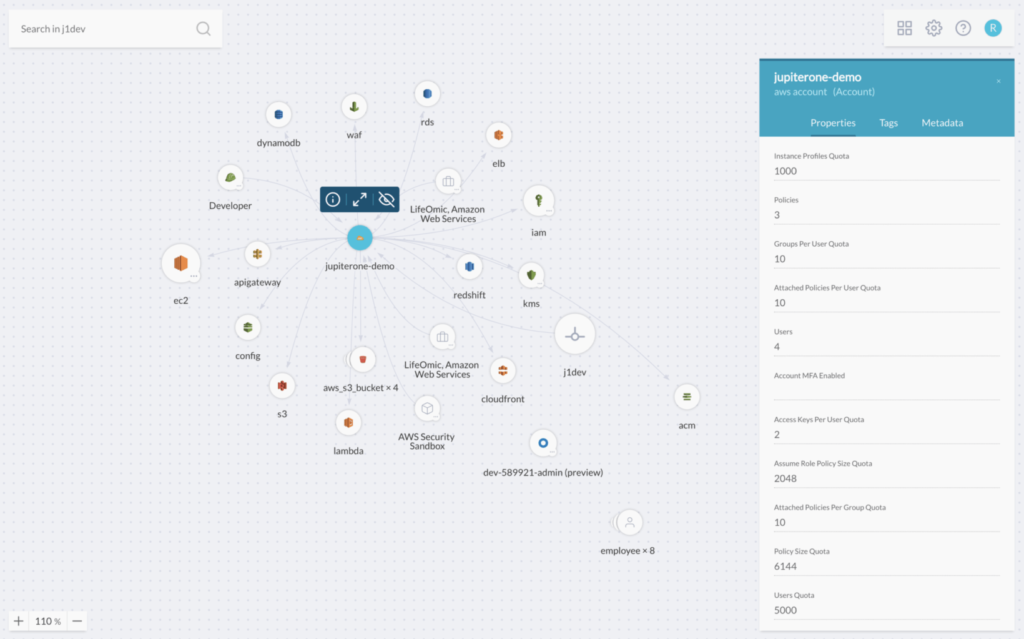
JupiterOne Galaxy View
They needed reactive alerting and vulnerability management
The JupiterOne Rules and Alerts Dashboard provided a “single pane of glass” to visualize, manage, and react to vulnerabilities.
For Adam, this was a vital need, “If someone reports that an IP address owned by Databricks has security concerns, we can establish a timeline for when we owned the IP address and whether the identified problems are ours. Most times, the problem is for an address that was ours but now belongs to someone else, and the security issue is not ours. Here the vulnerability belongs to one of their assets, and querying the graph makes it easy to assess what needs to be changed and who is responsible for changing it. This insight boosts confidence in our incident response process.”
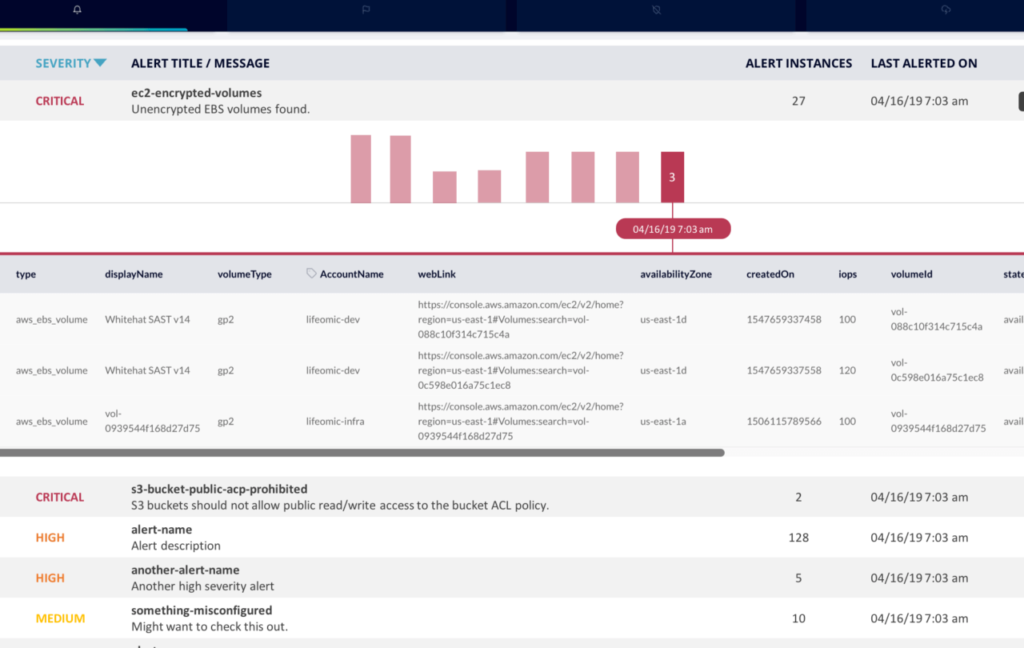
JupiterOne Rules and Alerts Dashboard
What was the end result?

A big surprise for the Databricks team was the easy deployment. In an hour and a half on the first day, they had ingested and confirmed the data coming into JupiterOne from their AWS resources.
Databricks gained faster insights and the ability to quickly and reliably know what S3 buckets existed, who owned them, and whether they were publicly accessible themselves or via another service.

With easy-to-use query tools and queries, Databricks was able to visualize all the tools and resources within a single location
Closing Security Thoughts
Organizations of all sizes need to understand their full ecosystem, reduce risks, increase awareness of their software bill of materials, and validate their security posture. This can be difficult with data scattered across multiple sources – on-premises and clouds.
Lastly, security should be viewed as an enabler of any strategic business decision that can open opportunities and build trust in the company in our customer-centric, acceleration economy.