CEO Thomas Kurian’s customer-centric approach, which he details in a one-on-one interview, has led to significant growth for Google Cloud, with Q4 revenue reaching $9.2 billion and a 25.7% growth rate.
Open-Source Software
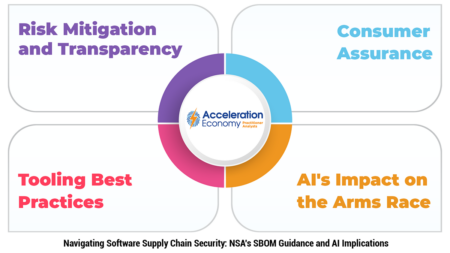
An exploration of the NSA’s software supply chain security guidance and how it can help organizations fortify overall cybersecurity.
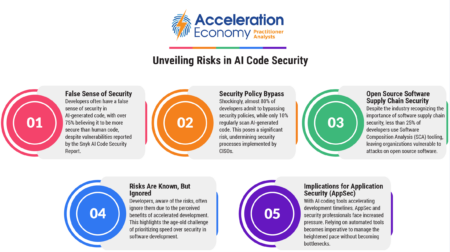
Snyk’s report on AI-generated code security shows how developers, lured by accelerated production, are unwittingly overlooking risks.
AI Index Report episode 13: Google prepares to launch its Gemini model; Writer secures funding to advance its LLM platform; and Granica announces Chronicle to better analyze data in cloud storage.
Microsoft forges strategic artificial intelligence (AI) partnerships with Meta and KPMG, driving innovation in its ecosystem and professional services.
OWASP has updated CycloneDX to support machine learning models, as the next generation of AI continues to enhance technology.
Google Cloud emerges as the preferred choice for over 70% of generative AI startups due to its advanced AI capabilities, reliable infrastructure, and open-source commitment.
AI Index Report episode 3: IBM releases watsonx.ai platform for enterprises; Databricks acquires MosaicML for $1.3 billion; and Amazon announces Amazon CodeWhisperer copilot.
Discover why closing the loop by fixing code is essential to effectively combat the security risk of hard-coded secrets.
Snyk provides developer-focused security for companies across every sector, enabling ongoing security improvements including reduced risk exposure.
The cybersecurity innovator Snyk caters to developers, ensuring that their code is secure as it’s written, and that their open-source software is monitored continuously.
Snyk and GitGuardian, two prominent security tools providers, collaborate to tackle cloud-native security challenges and bolster cybersecurity measures.
In this profile originally featured at the Generative Ai Digital Summit, Kenny Mullican dives into IBM’s new enterprise-ready data and AI platform watsonx.
The updated Endor Labs platform lets cybersecurity users assess open-source software using natural language search.
Kieron Allen explores how business analysts and data scientists benefit from the consolidated SAS Viya platform.
Bill Doerrfeld speaks with Perforce’s open-source evangelist on the benefits of creating a dedicated group to oversee open-source practices within organizations.
Tactical threat intelligence is gathering, analyzing, and sharing data to find cyber threats and figure out how to deal with them. Learn how to set up a program.
With DroidGPT, Endor Labs applies generative AI to software development to ensure open-source packages are current and secure.
In this special “on location” minute, Paul Swider shares his impressions from the third day of the HIMSS 2023 Global Health Conference and Exhibition in Chicago.
The cost of building and maintaining a technology ecosystem can be substantial, but there are ways to be smart about it, writes Janet Schijns.