Databricks’ AI Security Framework illuminates the path to secure and compliant AI adoption, addressing critical security risks across various stages of AI systems.
vulnerability
With Wiz CNAPP, CISOs embark on a new era of cloud security, leveraging integrated solutions to simplify operations and bolster defenses.
Nation-states, including China, Iran, North Korea, and Russia, are reported to be utilizing AI, particularly OpenAI’s platform, for malicious cyber activities.
Lacework’s latest innovation, AI Assist, transforms cloud-native security by offering personalized recommendations, natural language interactions, and expedited remediation.
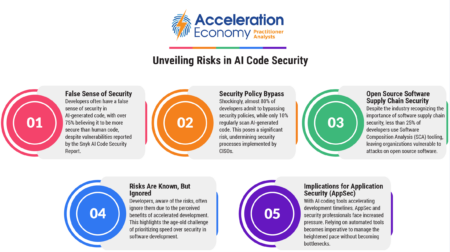
Snyk’s report on AI-generated code security shows how developers, lured by accelerated production, are unwittingly overlooking risks.
KPIs are crucial to understanding the performance of generative AI initiatives. Learn requirements that will help you build and apply KPIs effectively.
Discover the hidden risks embedded in AI code, including false security assumptions and a pattern of bypassing policies.
Wiz’s AI Security Posture Management (AI-SPM) addresses security and privacy concerns wrought by AI with comprehensive oversight, inventory management, and misconfiguration checks.
NetRise introduces Trace, an AI-powered feature revolutionizing software supply chain security, employing natural language processing to proactively identify and validate compromised assets and map relationships across the software supply chain.
NetRise’s AI-driven Trace feature transforms supply chain security, using semantic search and natural language processing to identify risks, offer context-rich insights, and create comprehensive asset graphs.
AI Index Report Ep 16: HeyGen uses AI and deep fakes for language translations; Wraithwatch gains funding for generative AI threat detection; and Microsoft launches its lightweight phi-1.5 model.
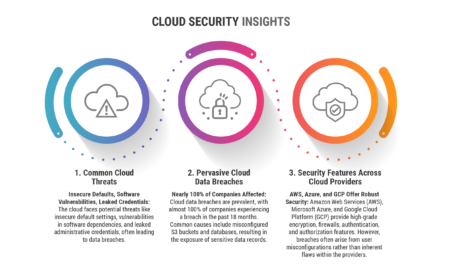
The big three cloud service providers AWS, Azure and Google Cloud share but also differ on features and vulnerabilities.
OWASP has updated CycloneDX to support machine learning models, as the next generation of AI continues to enhance technology.
Discover the top 10 Low-Code/No-Code vulnerabilities and how to secure rapid development environments.
There are several security risks associated with generative AI, including AI-powered social engineering attacks and evasion of traditional security defenses.
Process mining has several potential cybersecurity applications including incident investigation, anomaly detection, and detecting insider threats.
Fortinet’s “Cyber Threat Predictions for 2023” report examines the rise of ransomware, the mainstreaming of edge attacks, and the weaponization of AI.
GitGuardian and Snyk join forces to strengthen cloud-native security, enhance their developer-centric approach, and drive early risk mitigation in software development.
Snyk and GitGuardian, two prominent security tools providers, collaborate to tackle cloud-native security challenges and bolster cybersecurity measures.
Bill Doerrfeld explains how AI is improving endpoint threat detection and accelerating response times.