Generix has a strong focus on supply chain innovation, marked by strategic acquisitions and customer-focused offerings in warehouse management, transportation management, and more.
risk
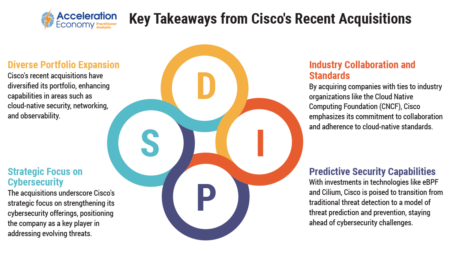
Cisco is positioning itself for the future of cloud-native cybersecurity and AI through acquisitions of Splunk and Isovalent.
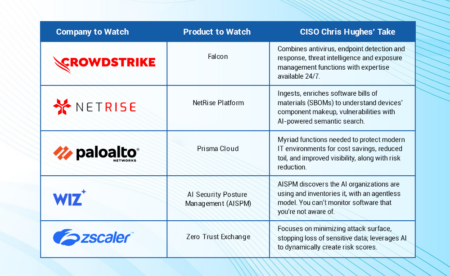
The top 5 cybersecurity products to watch in 2024 feature a healthy dose of generative AI and turnkey platforms, as well as supply chain and cloud protections.
KPIs are crucial to understanding the performance of generative AI initiatives. Learn requirements that will help you build and apply KPIs effectively.
Chris Hughes explains why sharing insights from threat intelligence with other senior execs can be a force multiplier in reducing organizational risk.
Wiz’s AI Security Posture Management (AI-SPM) addresses security and privacy concerns wrought by AI with comprehensive oversight, inventory management, and misconfiguration checks.
The chief data officer (CDO) and chief information security officer (CISO) should agree on encryption, role-based access, zero trust security, and data retention for effective business decisions and risk mitigation.
The Qlik Staige framework is a comprehensive approach to generative AI development, focused on structured data modernization, analytics insights, and rapid deployment.
As AI and NLP models move toward ubiquity, guardrails are needed to prevent the spread of misinformation and negative or unsavory information.
The upcoming SEC rules delve into cybersecurity transparency, incident reporting, and risk management procedures.
In part 2 of this free course from Acceleration Economy, learn how to successfully bridge the gap between buyers and sellers in the ever-evolving business technology landscape.
There are several security risks associated with generative AI, including AI-powered social engineering attacks and evasion of traditional security defenses.
Databricks hosted Microsoft CEO Satya Nadella at its customer event, and the two companies explained how they’re working on trustworthy AI and serving joint customers.
An Endor Labs study sheds light on ways to use ChatGPT in defensive cybersecurity. The company tapped AI to detect malware.
The increasing adoption of cloud services, particularly software-as-a-service (SaaS), has reshaped the role of the chief information security officer (CISO).
A proactive approach to SaaS security — starting with asset management — can protect against data misuse and other potential vulnerabilities.
Manual code reviews have limitations in addressing the risks of hard-coded secrets, leading to a critical need for automated analysis in securing the software development process.
Get a preview of “Selling to the New Executive Buying Committee,” an Acceleration Economy Course on vendor selection criteria for multi-cloud and SaaS cybersecurity.
The PMO helps organizations execute projects successsfully with demand-, program-, and project-management.
Janet Schijns discusses the power of strategic partnerships to navigate challenges, unlock opportunities, and achieve sustainable growth in the digital economy.