Google’s Project Naptime utilizes AI to enhance vulnerability discovery and management, offering promising advancements in cybersecurity.
risk
Oracle and Microsoft have expanded their multi-cloud partnership, offering Oracle’s Autonomous Database on Azure, allowing customers to accelerate the shutdown of outdated data centers and benefit from streamlined cloud migration.
An evaluation of centralized and decentrallized AI models concludes that a hybrid approach could be the best answer for future innovation and equitable outcomes.
The OWASP AI Cybersecurity & Governance Checklist outlines actionable recommendations for optimizing cybersecurity posture in the era of GenAI and LLM.
Lisa Rawls, a partner at KPMG, discusses its extensive collaboration with ServiceNow at the Knowledge 24 conference, with a focus on KPMG’s work with AI, its recent Partner of the Year award, and the importance of ethical AI implementation and strategic AI adoption for clients.
Google Cloud’s public criticism underscores Microsoft’s cybersecurity shortcomings, as detailed in a Cyber Safety Review Board report, prompting Microsoft’s efforts to address these issues.
Aviatrix is a multi-cloud security company offering a centralized control plane to manage configurations, networking, and security across various cloud service providers.
AI-driven cybersecurity advances pose both opportunities and threats, underscoring the critical need to fortify defenses against vulnerabilities and exploitations.
Databricks’ AI Security Framework illuminates the path to secure and compliant AI adoption, addressing critical security risks across various stages of AI systems.
With Wiz CNAPP, CISOs embark on a new era of cloud security, leveraging integrated solutions to simplify operations and bolster defenses.
Generix has a strong focus on supply chain innovation, marked by strategic acquisitions and customer-focused offerings in warehouse management, transportation management, and more.
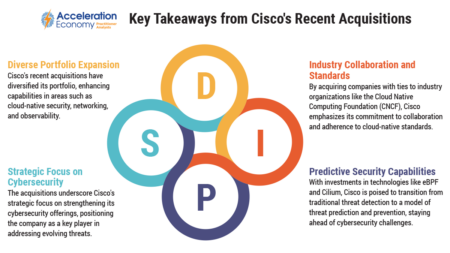
Cisco is positioning itself for the future of cloud-native cybersecurity and AI through acquisitions of Splunk and Isovalent.
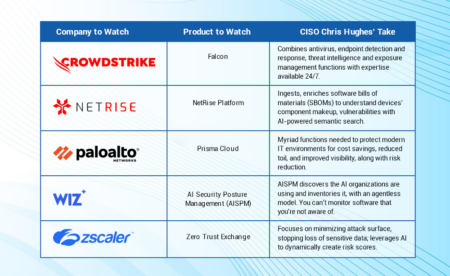
The top 5 cybersecurity products to watch in 2024 feature a healthy dose of generative AI and turnkey platforms, as well as supply chain and cloud protections.
KPIs are crucial to understanding the performance of generative AI initiatives. Learn requirements that will help you build and apply KPIs effectively.
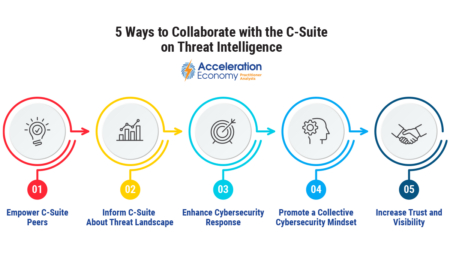
Chris Hughes explains why sharing insights from threat intelligence with other senior execs can be a force multiplier in reducing organizational risk.
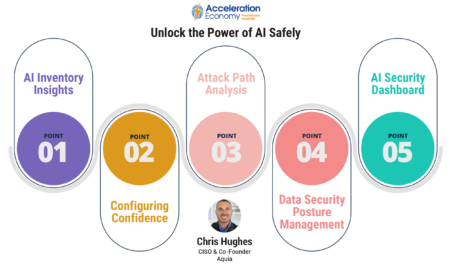
Wiz’s AI Security Posture Management (AI-SPM) addresses security and privacy concerns wrought by AI with comprehensive oversight, inventory management, and misconfiguration checks.
The chief data officer (CDO) and chief information security officer (CISO) should agree on encryption, role-based access, zero trust security, and data retention for effective business decisions and risk mitigation.
The Qlik Staige framework is a comprehensive approach to generative AI development, focused on structured data modernization, analytics insights, and rapid deployment.
As AI and NLP models move toward ubiquity, guardrails are needed to prevent the spread of misinformation and negative or unsavory information.
The upcoming SEC rules delve into cybersecurity transparency, incident reporting, and risk management procedures.