With Wiz CNAPP, CISOs embark on a new era of cloud security, leveraging integrated solutions to simplify operations and bolster defenses.
CISO
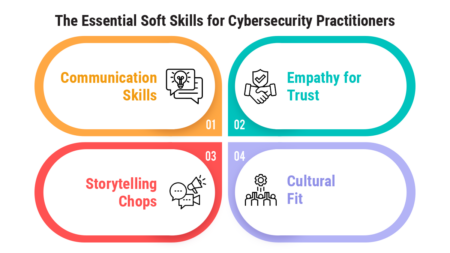
Mastering soft skills transforms cybersecurity professionals into strategic communicators, empathetic collaborators, and compelling storytellers.
Nation-states, including China, Iran, North Korea, and Russia, are reported to be utilizing AI, particularly OpenAI’s platform, for malicious cyber activities.
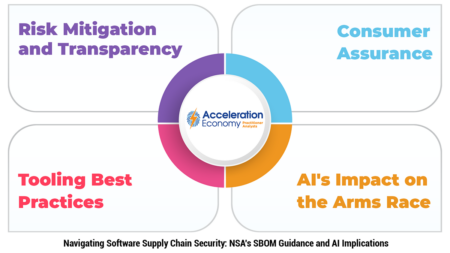
An exploration of the NSA’s software supply chain security guidance and how it can help organizations fortify overall cybersecurity.
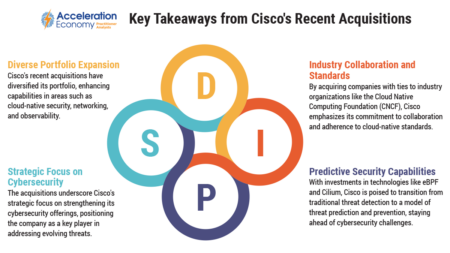
Cisco is positioning itself for the future of cloud-native cybersecurity and AI through acquisitions of Splunk and Isovalent.
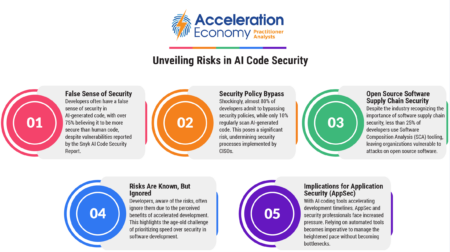
Snyk’s report on AI-generated code security shows how developers, lured by accelerated production, are unwittingly overlooking risks.
For CISOs and security leaders, grappling with the global ramifications of the EU AI Act becomes paramount, necessitating a proactive stance.
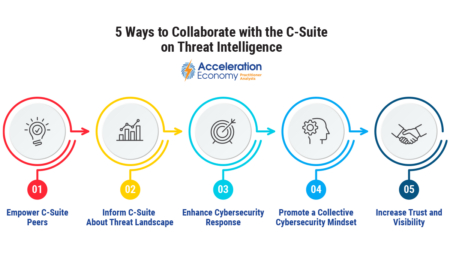
Chris Hughes explains why sharing insights from threat intelligence with other senior execs can be a force multiplier in reducing organizational risk.
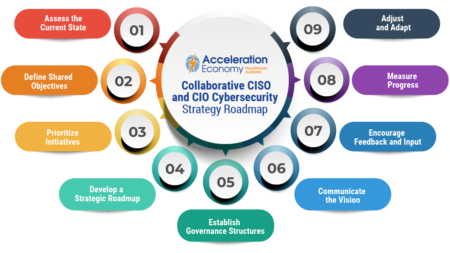
Establishing a strong working relationship between the CISO and the CIO is crucial for the overall success and security of a company, writes Kenny Mullican.
The chief data officer (CDO) and chief information security officer (CISO) should agree on encryption, role-based access, zero trust security, and data retention for effective business decisions and risk mitigation.
Ajay Sabhlok emphasizes the critical role of technology and collaboration in data management.
Technology partnerships are significant when it comes to harnessing AI capabilities, presenting both potential risks and opportunities, especially for smaller partners.
Trend Micro is integrating AI into its cybersecurity platform to empower organizations with enhanced capabilities.
There are several security risks associated with generative AI, including AI-powered social engineering attacks and evasion of traditional security defenses.
As cybersecurity teams face escalating demands and the need for faster responses, generative AI tcan help by scanning and summarizing vast amounts of data.
The increasing adoption of cloud services, particularly software-as-a-service (SaaS), has reshaped the role of the chief information security officer (CISO).
Manual code reviews have limitations in addressing the risks of hard-coded secrets, leading to a critical need for automated analysis in securing the software development process.
Trend Micro predicts that cloud security will be absorbed into overall security operations, following a familiar trend with past innovations.
Get a preview of “Selling to the New Executive Buying Committee,” an Acceleration Economy Course on top obstacles and concerns when moving to modern Cloud ERP from the CXO perspective.
Get a preview of “Selling to the New Executive Buying Committee,” an Acceleration Economy Course on top business and tech drivers for modern Cloud ERP.