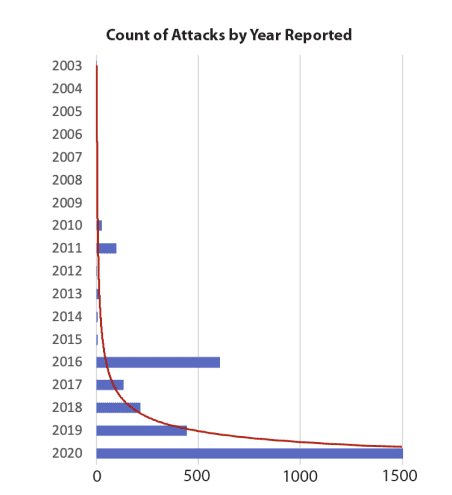
You would be hard-pressed to find a more-discussed topic in the cybersecurity industry in 2022 than the software supply chain. This is for good reason, too, as research and studies have shown that software supply chain incidents are increasing exponentially. While sources such as the Cloud Native Computing Foundation (CNCF) Catalog of Software Supply Chain Attacks show incidents dating back to the early 2000s, research from publications, such as Usenix, shows a tremendous uptick in software supply chain attacks.
Government Response
By now, everyone is familiar with the SolarWinds and Log4j incidents as well as the subsequent publication of the White House cybersecurity executive order. Now, the Office of Management and Budget (OMB) has published a memo, “Enhancing the Security of the Software Supply Chain through Secure Development Practices.”
The memo calls for broad, impactful actions which include mandating all federal agencies to prepare to start requiring self-attestation conformance statements from third-party software producers that they meet practices and activities identified in guidance such as the National Institute of Standards and Technology’s (NIST) Secure Software Development Framework (SSDF) as well as NIST’s Software Supply Chain Security Guidance. It also states agencies may request a Software Bill of Materials (SBOM) from software producers.
While, at first glance, this memo and associated guidance may seem irrelevant to the commercial industry, it is worth pointing out that the federal government is one of the largest procurers of software in aggregate in the world. This means that these requirements will inevitably have an impact on the software ecosystem. It’s also a sign to the commercial industry of how serious the federal government views the problem of software supply chain security.
It isn’t a stretch to suspect that many large commercial enterprise organizations may start to request similar levels of assurance and digital artifacts from their own software vendors, as well as implement guidance such as Secure Software Development Framework (SSDF) for their internal software development activities.
However, many of these requirements may not be practical for some of the small to mid-sized software vendors, particularly those without robust internal cybersecurity staff and expertise. This presents a challenge that may limit the federal government’s and potentially even large enterprises’ access to the innovative software solutions that small firms bring to the marketplace. But the rapid uptick in software supply chain attacks indicates this is a problem that simply can’t be ignored by the industry, either.
Where Open-Source Software Comes In
Much of this activity is tied to broader efforts to address an industry immaturity related to the consumption, use, and governance of open-source software (OSS). Industry organizations such as Open Source Security Foundation (OpenSSF) have launched efforts such as the Open Source Software Security Mobilization Plan to try and address the pervasive challenges industrywide when it comes to OSS security.
Most organizations simply don’t truly understand the extent of their OSS consumption or use, nor the potential risk associated with it. As highlighted by the OpenSSF plan, the industry overall has overarching problems that need to be addressed. This includes securing OSS production, improving vulnerability discovery and remediation, and shortening the ecosystems patching response time.
It’s no secret that OSS is driving major digital transformations and innovative capabilities in everything such as industrial control systems (ICS), manufacturing, retail, and even the federal government and national security applications. But without proper security practices, development, and governance, it also poses a systemic risk that, left unchecked, can cripple those same industries and have dire consequences for society as a whole. Much like the legend of the Gordian Knot, dealing with the challenges OSS poses may require innovative, outside-the-box thinking that traditionally hasn’t been applied to software or cybersecurity.
Want more cybersecurity insights? Visit the Cybersecurity channel: